Asset V2 Integration Guide#
Tip
To better understand the service and the terms covered in this guide please refer to the service lexicon
Detailed API documentation#
The Swagger API documentation is always up-to-date and lets you try out any query with your user session or an API-key.
Tip
Please read the General integration guide to learn the general concepts and common data structures used throughout the Argus API.
Integration Guide#
Note
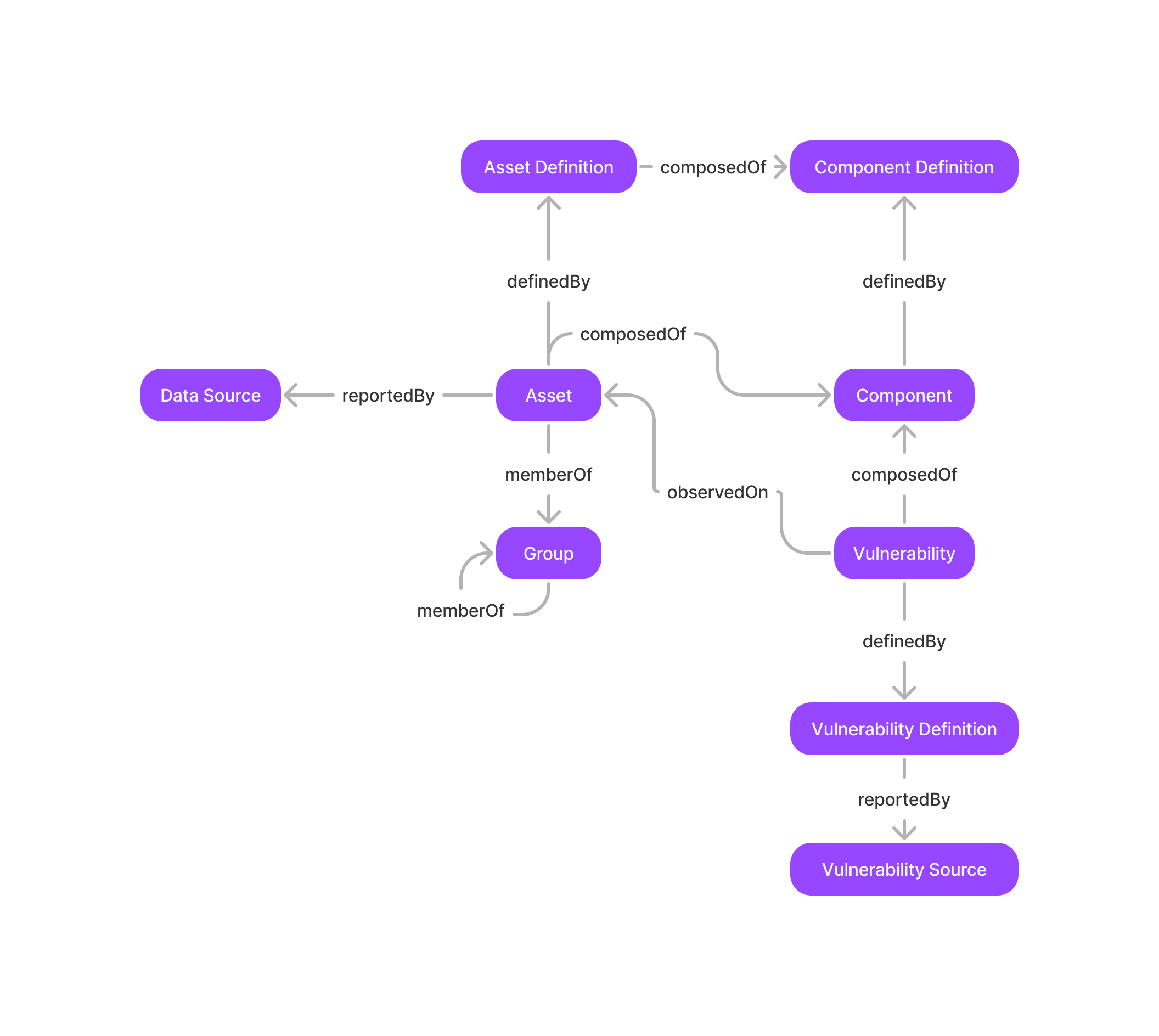
The Asset service’s data model is highly interconnected. Make sure to get a decent understanding of the interdependencies before reading the rest of this guide.
Data Model#
All endpoints for fetching, searching/listing, updating and deleting assets return the same data model.
See Swagger API documentation for details on the returned data model.
Creating Assets#
To create an asset you need to specify the shortName, name, criticality
triad, and asset definition. The asset definition describes what
components we can eventually attach to the asset and must already exist.
The optional forceIndex (default=false) option when creating, updating,
and deleting resources in the Asset service determines whether any
changes are immediately pushed to the search index i.e. making the
changes immediately searchable.
curl -X POST -H "Argus-API-Key: my/api/key" -H "Content-Type: application/json" https://api.mnemonic.no/assets/v2/asset -d '{
"customer": "mnemonic",
"shortName": "a1",
"name": "asset1",
"criticality": {
"confidentiality": "low",
"integrity": "high",
"availability": "unknown"
},
"assetDefinition": "assetDefinition1",
"components": [
{
"componentDefinition": "ipAddressComponentDefinition",
"value": "10.0.0.1"
}
]
}'
Asset Components#
Components, represent a piece of information about an Asset are defined by an Asset Component Definition. To be able to set a Component on an Asset it must be identifiable by its unique shortname or ID and defined on the Asset’s Definition.
Component Definitions include the following fields:
shortName- unique human readable identifiername- non-unique display nametype- the expected/permitted data type of the value of components defined by this definitionvisibility- whether components defined by this definition are appropriate for assets, vulnerabilities, or both
Important
The value of any component created with this definition will be validated against the type and rejected, if invalid.
When creating components, it’s possible to explicitly indicate that a component is to be considered unique. I.e. the Asset can only contain a single Component of that type. When creating or updating Assets, the service will reject the request if it contains multiple unique components of the same type, or any duplicate values. If the request is valid, the following outcomes are possible:
The Asset does not contain any active components, unique or otherwise, of the given type - the new unique component is added
The Asset contains active non-unique components of the given type - all existing components are expired and the new unique component is added
The Asset contains an active unique component of the given type - the existing component is expired and the new unique component is added
The Asset contains an active unique component of the given type while the submission is non-unique - the existing component is expired and the new component is added and flagged as unique
Enum Type Components#
The enum type component is a special case of component. It enables asset admin users to define a set of allowed values a given enum component can have. To check which values are allowed for a given component definition use the dedicated endpoint:
curl -X 'GET' \
'https://api.mnemonic.no/assets/v2/component/definition/vehicles/values?offset=0&limit=25&includeDeleted=true'
This returns the set of allowed values for components using this definition, which looks something like the following:
Simplified enum components response
{
"responseCode": 200,
"limit": 25,
"offset": 0,
"count": 3,
"metaData": {},
"messages": [],
"data": [
{
"value": "BICYCLE",
"localisedDisplayValue": "Bicycle",
"localisedDisplayValues": {
"english": "Bicycle",
"norwegian": "Sykkel"
}
},
{
"value": "BIKE",
"localisedDisplayValue": "Bike",
"localisedDisplayValues": {
"english": "Bike",
"norwegian": "Sykkel"
},
"flags": [
"deleted"
]
},
{
"value": "CAR",
"localisedDisplayValue": "Car",
"localisedDisplayValues": {
"english": "Car",
"norwegian": "Bil"
}
}
],
"size": 3
}
Attempts to create an asset with an enum component with either a deleted or invalid value will be rejected.
Fetching Assets#
We can fetch individual Assets by identifying them by their ID or unique (per customer) shortName field.
curl -H "Argus-API-Key: my/api/key" https://api.mnemonic.no/assets/v2/asset/{assetIdOrShortName}
If successful, the above invocation will return the Asset basic model:
{
"data": {
"id": "0005cd25-2be2-44fa-a260-b0f735c9797a",
"customer": { "id":1, "shortName":"mnemonic", ...},
"shortName":"a1",
"name":"asset1",
"description":"This is the description for this asset",
"assetDefinition": {
"id": "00000000-0000-0000-0000-000000000001",
"domain": {
"id": 1,
"name": "MNEMONIC"
},
"shortName": "HostAsset",
"name": "HostAsset"
},
"components": [...],
...
}
}
Updating Assets#
Updating the basic fields of an asset is done with a PUT request to the Asset’s, identified by its ID or unique short name, endpoint. Asset components can also be added, and removed, via this request.
If no parameters are provided, no changes are performed. Similarly, for
any parameter sent to this endpoint, a null value will cause no change
to the current value.
curl -X PUT -H "Argus-API-Key: my/api/key" -H "Content-Type: application/json" https://api.mnemonic.no/assets/v2/asset/{assetIdOrShortName} -d '{
"criticality": {
"confidentiality": "high",
"integrity": "low",
"availability": "high"
},
"addComponents": [
{
"componentDefinition": "cd1",
"value": "componentValue",
"ttl": 0
}
],
"deleteComponents": [
"0005cd25-2be2-44fa-a260-b0f735c9797a",
"0005cd25-2be2-44fa-a260-b0f735c9797a"
]
}'
Importing Assets#
The endpoint should be used when importing a large number of assets where you don’t know if the assets are new or already exist in the database. A good example would be when importing a scanner report. It allows the ingestion of individual assets as well as their corresponding components and observations in a single request, and will handle eventual merge conflicts. The endpoint responds with the id of the asset, and whether it is new or already exists in the database, without a guarantee that processing has completed yet.
To import an asset you need to specify how the service should identify assets. This is specified in assetIdentification.
assetDefinition is always required, but the other fields depend on the chosen identification strategy.
If set to asset, the shortName or id of the asset must be given. If set to component,
an identification component will be used. identificationComponent and identificationComponentValue is then required.
If no asset is identified with the given strategy, the resulting actions depend on the chosen strategy. If identifying
by component or shortName we create a new asset, if identifying by id we reject the import request.
assetName is only used to set new assets’ display name, and if not given, the generated asset id will be used.
Asset components connected to the asset are not required, but can be added
with the components field. Components added via imports are subject to the same validation as when
adding/updating individual Assets via the add and update endpoints. I.e. the value must be appropriate for the type.
The same applies to observed instances of Vulnerabilities on the asset which can be added with observations.
The vulnerability field must be populated for each observation and expects a vulnerability definition ID (UUID) or vulnerabilityID
e.g. MV101-123456. For those observations in the import whose vulnerability field does not resolve to a known vulnerability definition
the observation will be created without a vulnerability definition.
The data model for the observations is best described in Creating Vulnerabilities.
customer and dataSource are always required. dataSource provides the merge strategy
to be used when handling merge conflicts.
curl -X POST -H "Argus-API-Key: my/api/key" -H "Content-Type: application/json" https://api.mnemonic.no/assets/v2/asset -d '{
"assetName": "myAsset",
"dataSource": "datasource1",
"customer": "mnemonic",
"assetIdentification": {
"strategy": "component",
"asset": "",
"assetDefinition": "assetDefinition1",
"identificationComponent": "componentDefinition1",
"identificationComponentValue": "identificationComponentValue1"
},
"components": [
{
"componentDefinition": "componentDefinition2",
"value": "componentValue1"
}
],
"observations": [
{
"vulnerability": "COVID-19",
"severity": "high",
"rawOutput": "rawOutput",
"cvss": 0,
"observationDescription": "description",
"observationReferences": [
""
],
"components": [
{
"component": "string",
"value": "string"
}
]
}
]
}'
Merge resolution strategies#
The strategies are defined by the sameSourceMergeResolutionStrategy and otherSourceMergeResolutionStrategy
fields in the /assets/v2/datasource endpoint. We differentiate between conflicts from the same data source
and different data sources.
The current strategies are:
append: the new data is added to the asset. The existing data is kept intact.
reject: the new data is ignored. The existing data is kept intact.
replace: the new data replaces the old data. The existing data is deleted.
expire: if the existing data has expired, meaning it’s time to live has passed, it is set expired. The new data is added - replacing the existing data. If the existing data has not expired, we reject the new data.
Import Status#
As this is an asynchronous endpoint the API will return a response while the request is still being processed. The import response consists of
status: Whether the asset already existed in the database or is new - one of ‘existingAsset’ or ‘newAsset’
asset: The id of the existing asset or the id assigned to the new asset being generated by the import
jobID: The id of the job processing the request - can be used to fetch the status and eventual result of the import
We can then fetch the status of a specific import job using its ID:
curl -X GET -H "Argus-API-Key: my/api/key" https://devapi.mnemonic.no/assets/v2/import/status/<jobID>
The response contains the status of the job (‘prepared’, ‘active’, ‘failed’, ‘success’, ‘timeout’) and information about the number of components/observations processed by the import.
Searching for Assets#
Assets are searchable by their basic properties and their relationships with other resources in the Asset Service e.g. parent or ancestor group(s). All searches are restricted to assets belonging to customers for whom the current user has at least read permission.
curl -X POST -H "Argus-API-Key: my/api/key" -H "Content-Type: application/json" https://api.mnemonic.no/assets/v2/asset/search -d '{
"sortBy": [
"lastUpdatedTimestamp"
],
"keywords": [
"content"
],
"keywordFieldStrategy": [
"description"
]
"parent": [
"assetGroupShortName"
],
...
}'
Asset Statistics#
Warning
The Asset Statistics API is not completely stable i.e. new features are still under development. Please contact Mnemonic directly for clarification.
The Asset statistics endpoint allows a user to retrieve quantitative data about a set of assets that match certain search criteria.
The statistics request supports the same search criteria as the search endpoint; the statistics criteria then apply to the results of the search.
The statistics request itself is composed of 3 key components:
field aggregation - the field(s) by which we want to group the resulting assets and structure the response
range metrics - return counts for assets matching the defined timestamp filters
statistics metrics - return basic statistical data (min, max, median, avg, e.t.c) for asset numerical fields e.g. CVSS or vulnerability count
For example, we could ask for vulnerability statistics for assets created within the last month and also determine which of them have been updated during the same time period, aggregated by the types of assets and the groups to which they belong:
curl -X 'POST' \
'https://api.mnemonic.no/assets/v2/asset/statistics' \
-H 'accept: application/json' \
-H 'Content-Type: application/json' \
-H 'Argus-API-Key: my/api/key' \
-d '{
"startTimestamp": "now-1month",
"endTimestamp": "now",
"timeFieldStrategy": [
"createdTimestamp"
],
"fieldAggregation": [
{
"field": "assetGroup",
"limit": 25
},
{
"field": "assetDefinition",
"limit": 25
}
],
"rangeMetric": [
{
"name": "updatedThisWeek",
"field": "lastUpdated",
"startTimestamp": "now-1week",
"endTimestamp": "now"
}
],
"statisticsMetric": [
{
"field": "vulnerabilities"
}
],
"includeDeleted": false
}'
The response’s structure is a unidirectional tree where the branches represent unique field aggregation values i.e. in this example groups and definitions.
Each branch consists of the count of assets within the branch and metadata containing
identifier - the unique ID of the object
shortName - the unique human/machine readable identifier
name - the human readable non-unique identifier
type - the type (assetGroup or assetDefinition in this example) of the metadata
Each branch then potentially contains buckets, which represent the next layer in the tree.
The leaves contain the actual metrics response e.g.:
{
"metadata": {
"identifier": "assetGroupUUID",
"shortName": "assetGroupShortName",
"name": "Asset Group Name",
"type": "assetGroup"
},
"count": 291,
"buckets": [
{
"metadata": {
"identifier": "00000000-0000-0000-0000-000000000001",
"shortName": "HostAsset",
"name": "Host Asset",
"type": "assetDefinition"
},
"count": 291,
"buckets": [
],
"rangeMetrics": [
{
"key": "updatedThisWeek",
"count": 1,
"startTimestamp": 1681198844900,
"endTimestamp": 1681803644900
}
],
"statisticsMetrics": [
{
"key": "vulnerabilities",
"count": 291,
"min": 0,
"max": 441,
"avg": 48.67697594501718,
"sum": 14165
}
]
}
],
"rangeMetrics": [
],
"statisticsMetrics": [
]
}
Creating Asset Groups#
To create an asset you need to specify the shortName, name, and
criticality triad.
curl -X POST -H "Argus-API-Key: my/api/key" -H "Content-Type: application/json" https://api.mnemonic.no/assets/v2/group -d '{
"customer": "mnemonic",
"shortName": "ag1",
"name": "assetGroup1",
"criticality": {
"confidentiality": "low",
"integrity": "high",
"availability": "unknown"
}
}'
Dynamic Asset Groups#
Dynamic Asset Groups are a special type of groups which can only contain Assets, not other groups. Dynamic Groups can be created using the normal ‘create Asset Group’ endpoint, but some additional fields are required:
dynamic: this flag needs to be set to ‘true’, or, if the filter is filled out correctly, it will be set to true automatically
owner: if not filled out will default to the user making the request
populateDynamicGroup: indicates if the task refreshing the group should be run right away
canContainAssets: if the dynamic flag is ‘true’ or the filter is filled out correctly, this flag will automatically be set to true,
filter: assets that are found with the criteria saved in this search filter will be automatically added to the group,
Note: two types of filters are supported:
asset search filter populates the group directly with results filtered in addition by the group customer
observation search filter resolves the observations into assets, applies group customer filtering and thus populates the group.
Group customer is used as an additional filtering criteria for the assets, so the group contains only the assets of the customer for which it was created, even if the filter does not include a customer. So, the same search filter can be reused to create groups for different customers.
curl -X 'PUT' \
'https://api.mnemonic.no/assets/v2/group' \
-H 'accept: application/json' \
-H 'Argus-API-Key: my/api/key' \
-d '{
"customer": "mnemonic",
"shortName": "agDynamic",
"owner": "userIdOrShortname"
"name": "assetGroupDynamic",
"dynamic": true,
"filter": "filterUUIDorShortname",
"populateDynamicGroup": true
}
}'
The dynamic groups are managed automatically, so attaching/detaching assets to these groups will be effective only until the next update cycle for the group is run. The refresh task is triggered every 30 minutes, but the groups are refreshed only if their last dynamic update happened over 1h ago.
Filter management is done with JsonObject service. Relevant object types for this usecase are ‘assetSearchCriteria’ and ‘assetObservationSearchCriteria’ To list filters available for dynamic groups setup, use the GET by type endpoint in the JsonObject Service:
curl -X 'GET' \
'https://api.mnemonic.no/jsonobject/v1/object/AssetSearchCriteria?includeData=false&includeDeleted=false&limit=25&offset=0' \
-H 'accept: application/json' \
-H 'Argus-API-Key: my/api/key'
Attaching Assets to a Group#
To add Assets to a Group submit their IDs or short names to the group’s attach endpoint.
curl -X POST -H "Argus-API-Key: my/api/key" -H "Content-Type: application/json" https://api.mnemonic.no/assets/v2/group/groupShortNameOrID/assets -d '{
"assets": [
"asset1",
"asset2"
]
}
}'
Searching for Groups#
Similar to Assets, Groups are searchable by their basic properties and by their relationships to other objects in the Asset Service. groups e.g. parent, ancestor, or child group(s) and member assets. All searches are restricted to groups belonging to customers for whom the current user has at least read permission.
curl -X POST -H "Argus-API-Key: my/api/key" -H "Content-Type: application/json" https://api.mnemonic.no/assets/v2/group/search -d '{
"sortBy": [
"lastUpdatedTimestamp"
],
"keywords": [
"content"
],
"keywordFieldStrategy": [
"description"
]
"parent": [
"assetGroupIDOrShortName"
],
"asset": [
"assetIdOrShortName"
],
"child": [
"assetGroupIDOrShortName"
]
...
}'
Creating Vulnerabilities#
To create a Vulnerability you need to specify the asset (identified by its UUID or shortname) on which the vulnerability was observed, its vulnerability definition.
CVSS and Severity values are optional when creating a vulnerability. If these are not specified, the
values from the relevant Vulnerability Definition are used. If it is necessary to manually put in different
values for the specific observation, the observation will be marked with flags overwrittenDefinitionCVSS or
overwrittenDefinitionSeverity depending on which value is adjusted. Please note that ‘overwritten’ value will no longer be
updated when the Vulnerability Definition values change. If only CVSS is provided the Severity is calculated based
on CVSS value.
CVSS/Severity - Mapping
CVSS |
Severity |
|---|---|
0 |
INFO |
< 4 |
LOW |
< 7 |
MEDIUM |
< 9 |
HIGH |
<= 10 |
CRITICAL |
The optional forceIndex option (default=false) will instruct the service to refresh the search index such that new vulnerabilities are immediately searchable. Like Assets, Vulnerabilities can be created bound to specific components.
The time to live (TTL) field determines how long the component information is considered valid. Ideally it should be longer than the scan interval so that component information is not invalidated before it can be updated. Please see the Swagger API for how the other fields are handled or determined if not provided.
Specify Customer#
NB: If the request does not explicitly specify the Customer who owns the Asset on which the Vulnerability was detected and the Asset was defined by its short name then the service will attempt to resolve the Asset based on the requesting user’s Customer. As Asset shortNames are unique per customer it’s possible that this request might fail.
curl -X POST -H "Argus-API-Key: my/api/key" -H "accept: application/json"
"https://api.mnemonic.no/assets/v2/vulnerability" -d '{
"customer": "mnemonic",
"asset": "internalAsset",
"vulnerability": "vulnerabilityDefinition",
"components": [
{
"componentDefinition": "cpeComponentDefinition",
"value": "cpe:2.3:o:microsoft:windows:2008:r2",
"ttl": 0
}
],
"cvss": 3,
"severity": "low",
"rawOutput": "output from scanner",
"ttl": 0
}'
Fetching Vulnerabilities#
To fetch a single Vulnerability you need to provide its UUID:
curl -H "Argus-API-Key: my/api/key" https://api.mnemonic.no/assets/v2/vulnerability/53477c72-f4c8-4929-bc05-3a8c7d4ba7a2
A successful request will return the Vulnerability’s data model:
{
"id": "53477c72-f4c8-4929-bc05-3a8c7d4ba7a2",
"customer": {
"id": 1,
"name": "mnemonic",
"shortName": "mnemonic",
"domain": {
"id": 1,
"name": "MNEMONIC"
}
},
"asset": {
"id": "4cb3797b-35f6-4ca7-8102-46e8a3946829",
"customer": {
...
},
"shortName": "GraphQLAsset_2",
"name": "Asset 2 - Asset V2 Test"
},
"vulnerabilityID": "COVID-19",
"vulnerabilityDefinition": null,
"components": [],
"cvss": 8.8,
"severity": "high",
"resolution": "unresolved",
"resolutionTimestamp": 0,
"resolvedByUser": null,
"resolutionComment": null,
"rawOutput": null,
"firstSeenTimestamp": 1596539880803,
"lastSeenTimestamp": 1596539880803,
"firstSeenByUser": {
"id": 8982,
"shortName": "testUser",
"name": "Test User",
"domain": null,
"customer": {
...
},
"type": "user"
},
"lastSeenByUser": {...},
"ttl": 0,
"expireTimestamp": 0,
"createdTimestamp": 1596539880803,
"createdByUser": {...},
"lastUpdatedTimestamp": 1596539880803,
"lastUpdatedByUser": {...},
"deletedTimestamp": 0,
"deletedByUser": null,
"flags": []
}
Resolving Vulnerabilities#
Although actually resolving a Vulnerability is not handled by Argus, updating a Vulnerability’s resolution status is an important step in the Vulnerability management process.
When resolving a Vulnerability permitted resolution statuses are:
accepted - the Vulnerability is known and will not be handled
temporarilyAccepted - the Vulnerability is known and will be handled at a later date
falsePositive - not a Vulnerability
serviceNotAvailable
noLongerVulnerable - the Vulnerability has been handled
To resolve a vulnerability simply submit a resolution request to the vulnerability’s resolution endpoint:
curl -X PUT -H "Argus-API-Key: my/api/key" "accept: application/json" -H "Content-Type: application/json" \
"https://devapi.mnemonic.no/assets/v2/vulnerability/4cb3797b-35f6-4ca7-8102-46e8a3946829/resolve" -d \
'{
"resolution": "accepted",
"comment": "cannot resolve now"
}'
Resolving Vulnerabilities by Search Request or Set#
Although actually resolving a Vulnerability is not handled by Argus, updating a Vulnerability’s resolution status is an important step in the Vulnerability management process.
It is possible to change resolution on several Vulnerabilities with one request. Calling the dedicated endpoint will create a service task running in the background, which will iterate over provided ids and update the Vulnerabilities according to the request.
The same constraints for the request values are applicable as for search observation and resolve single endpoints.
curl -X 'PUT' \
'https://api.mnemonic.no/assets/v2/vulnerability/bulk/resolve/async' \
-H 'accept: application/json' \
-H 'Argus-API-Key: my/api/key' \
-d '{
"observations": [
"3fa85f64-5717-4562-b3fc-2c963f66afa6", "3de85f64-5717-7562-b3fc-2c963f66afa6"
],
"resolution": "accepted",
"resolutionExpiryTimestamp": "0",
"comment": "well resolved"
}'
This endpoint returns a BulkResolveObservationsTaskCreated response, containing the created task id. The task id can be used to abort the task or to fetch its status via the Service Task management endpoints.
Note
Aborting the task will not cause a rollback of the changes that were already made.
Recasting Vulnerabilities#
It is possible to change Severity and CVSS on several Vulnerabilities with one request. Calling the dedicated endpoint will create a running in the background service task, which will iterate over provided ids and update the Vulnerabilities according to the request.
Please note that this operation will mean that Severity and CVSS for all the Vulnerabilities in the request will not be managed from the definition level anymore.
curl -X 'PUT' \
'https://api.mnemonic.no/assets/v2/vulnerability/bulk/recast' \
-H 'accept: application/json' \
-H 'Argus-API-Key: my/api/key' \
-d '{
"observations": [
"3fa85f64-5717-4562-b3fc-2c963f66afa6", "3de85f64-5717-7562-b3fc-2c963f66afa6"
],
"severity": "critical",
"cvss": 10
}'
This endpoint returns a BulkRecastObservationsTaskCreated response, containing the created task id. The task id can be used to abort the task or to fetch its status via the Service Task management endpoints.
Searching for Vulnerabilities#
Vulnerability are searchable by their basic properties and their direct relationship with the asset on which they were detected. All searches are restricted to Vulnerabilities on Assets belonging to the customer(s) for whom the requesting user has permission to access. Unlike Asset and Asset Groups, Vulnerabilities currently have no keyword fields. Only exact matches will return results.
{
"sortBy": [
"vulnerabilityID"
],
"startTimestamp": 0,
"endTimestamp": 0,
"timeFieldStrategy": [
"all"
],
"timeMatchStrategy": "any",
"userFieldStrategy": [
"lastUpdatedByUser"
],
"user": [
"testUser"
],
"asset": [
"myVeryImportantAsset"
],
"customer": [
"mnemonic"
],
"severity": "info",
"resolution": "unresolved",
"minimumCvss": 1,
"maximumCvss": 2,
"includeRawOutput": false,
"limit": 0,
"offset": 0,
"includeDeleted": false
}
To, for example, retrieve all open Vulnerabilities created on Assets belong to a particular Customer for the last week you could submit the following query:
{
"sortBy": [
"createdTimestamp"
],
"customer": [
"customerIdOrShortName"
],
"resolution": "unresolved",
"startTimestamp": "startOfWeek - 1 week",
"endTimestamp": "startOfWeek"
}
Creating Vulnerability Definitions#
A Vulnerability Definition is a general description of a Vulnerability. It contains a subset of CVE data as well as other Mnemonic generated data. Vulnerability observations are instances of a Vulnerability Definition. Vulnerability definitions are not specific to a particular asset or customer and contain globally available unrestricted information.
To create a Vulnerability Definition you need to specify its source (identified by its UUID or shortname) and vulnerability definition identifier (for example plugin ID from vulnerability scanner). It is also required to provide CVSS for the vulnerability definition. If a severity is not specified, it will be assigned based on the submitted CVSS value using the following mapping:
CVSS/Severity - Mapping
CVSS |
Severity |
|---|---|
0 |
INFO |
< 4 |
LOW |
< 7 |
MEDIUM |
< 9 |
HIGH |
<= 10 |
CRITICAL |
Permissions required: addVulnerabilityDefinition
curl -X 'POST' \
'https://api.mnemonic.no/assets/v2/vulnerability/definition?forceIndex=false' \
-H 'accept: application/json' \
-H 'Content-Type: application/json' \
-H "Argus-API-Key: my/api/key" \
-d '{
"vulnerabilitySource": "string",
"vulnerabilityID": "string",
"name": "string",
"description": "string",
"solution": "string",
"conclusion": "string",
"references": [
"string"
],
"exploitAvailable": true,
"exploitAvailableTimestamp": 0,
"severity": "info",
"cvss": 0
}'
Additional note on Severity and CVSS: Values in the vulnerability definition will be used to populate newly created vulnerabilities (observations) relevant to the given definition. The changes on vulnerability definition update for Severity and CVSS values will be propagated in an async manner to the relevant observations.
Fetching Vulnerability Definitions#
To fetch a single Vulnerability Definition it’s necessary to provide definition UUID or identifier of vulnerability (for example “MV301-OS-CIS-2.3.10.3-129”)
Permissions required: viewVulnerabilityDefinition
curl -X 'GET' \
'https://api.mnemonic.no/assets/v2/vulnerability/definition/MV301-OS-CIS-2.3.10.3-129' \
-H 'accept: application/json' \
-H "Argus-API-Key: my/api/key"
A successful request will return the Vulnerability Definition’s data model:
Vulnerability Definition - data model
{
"id": "3fa85f64-5717-4562-b3fc-2c963f66afa6",
"vulnerabilitySource": {
"id": "3fa85f64-5717-4562-b3fc-2c963f66afa6",
"shortName": "string",
"name": "string"
},
"vulnerabilityID": "string",
"name": "string",
"description": "string",
"solution": "string",
"conclusion": "string",
"references": [
"string"
],
"exploitAvailableTimestamp": 0,
"createdTimestamp": 0,
"createdByUser": {
"id": 0,
"shortName": "string",
"name": "string",
"domain": {
"id": 0,
"name": "string"
},
"customer": {
"id": 0,
"name": "string",
"shortName": "string",
"domain": {
"id": 0,
"name": "string"
}
},
"type": "user"
},
"lastUpdatedTimestamp": 0,
"lastUpdatedByUser": {
"id": 0,
"shortName": "string",
"name": "string",
"domain": {
"id": 0,
"name": "string"
},
"customer": {
"id": 0,
"name": "string",
"shortName": "string",
"domain": {
"id": 0,
"name": "string"
}
},
"type": "user"
},
"deletedTimestamp": 0,
"deletedByUser": {
"id": 0,
"shortName": "string",
"name": "string",
"domain": {
"id": 0,
"name": "string"
},
"customer": {
"id": 0,
"name": "string",
"shortName": "string",
"domain": {
"id": 0,
"name": "string"
}
},
"type": "user"
},
"flags": [
"deleted"
],
"severity": "info",
"cvss": 0
}
Updating Vulnerability Definition#
It’s possible to update the Vulnerability Definition by providing its UUID or identifier of vulnerability (for example “MV301-OS-CIS-2.3.10.3-129”)
Permissions required: updateVulnerabilityDefinition
curl -X 'PUT' \
'https://api.mnemonic.no/assets/v2/vulnerability/definition/MV301-OS-CIS-2.3.10.3-12?forceIndex=false' \
-H 'accept: application/json' \
-H 'Content-Type: application/json' \
-H "Argus-API-Key: my/api/key" \
-d '{
"name": "string",
"description": "string",
"solution": "string",
"conclusion": "string",
"addReferences": [
"string"
],
"deleteReferences": [
"string"
],
"exploitAvailable": true,
"exploitAvailableTimestamp": 0,
"cvss": 10,
"severity": "info"
}'
The forceIndex option should be set to true only if the use case requires the definition to be immediately
searchable. Without this option the change should be visible within seconds.
Deleting Vulnerability Definition#
It’s possible to delete the Vulnerability Definition by providing its UUID or identifier of vulnerability (for example “MV301-OS-CIS-2.3.10.3-129”)
Permissions required: deleteVulnerabilityDefinition
curl -X 'DELETE' \
'https://api.mnemonic.no/assets/v2/vulnerability/definition/MV301-OS-CIS-2.3.10.3-12?forceIndex=false' \
-H 'accept: application/json' \
-H "Argus-API-Key: my/api/key"
The forceIndex option, should be set to true only if the use case requires the definition’s status change to be
immediately reflected in the search results. Without this option the change should be visible within seconds.
Searching for Vulnerabilities#
Vulnerability Definitions are searchable by keywords. Searching for vulnerability definitions can be done using the
simple search GET endpoint or the advanced search POST endpoint.
Please read the General integration guide to learn about general concepts for search
endpoints.
Permissions required: viewVulnerabilityDefinition.
Simple search#
For simple search it is possible to search for vulnerability definitions by keyword and or Vulnerability ID
(identifier). The search can also be filtered by startTimestamp and endTimestamp for when the vulnerability was
first and last observed.
curl -X 'GET' \
'https://api.mnemonic.no/assets/v2/vulnerability/definition?vulnerabilityID=string&limit=25&offset=0&includeDeleted=false&startTimestamp=0&endTimestamp=0&keywords=string' \
-H 'accept: application/json' \
-H "Argus-API-Key: my/api/key"
Other parameters include limit, offset, sort and includeDeleted.
Advanced search#
Advanced search has access to all possible filtering parameters for vulnerability definition, and follows the general advanced search structure as described in the General integration guide.
Vulnerability Definition search - request model
curl -X 'POST' \
'https://api.mnemonic.no/assets/v2/vulnerability/definition/search' \
-H 'accept: application/json' \
-H 'Content-Type: application/json' \
-H "Argus-API-Key: my/api/key" \
-d '{
"sortBy": [
"name"
],
"keywords": [
"string"
],
"keywordFieldStrategy": [
"all"
],
"keywordMatchStrategy": "any",
"vulnerabilitySource": [
"string"
],
"vulnerabilityID": [
"string"
],
"vulnerabilityDefinition": [
"string"
],
"startTimestamp": "string",
"endTimestamp": "string",
"timeFieldStrategy": [
"all"
],
"timeMatchStrategy": "any",
"userFieldStrategy": [
"all"
],
"user": [
"string"
],
"includeFlags": [
"deleted"
],
"excludeFlags": [
"deleted"
],
"severity": [
"info"
],
"maximumCvss": 10,
"minimumCvss": 10,
"subCriteria": [
{
"keywords": [
"string"
],
"keywordFieldStrategy": [
"all"
],
"keywordMatchStrategy": "any",
"vulnerabilitySource": [
"string"
],
"vulnerabilityID": [
"string"
],
"vulnerabilityDefinition": [
"string"
],
"startTimestamp": "string",
"endTimestamp": "string",
"timeFieldStrategy": [
"all"
],
"timeMatchStrategy": "any",
"userFieldStrategy": [
"all"
],
"user": [
"string"
],
"includeFlags": [
"deleted"
],
"excludeFlags": [
"deleted"
],
"severity": [
"info"
],
"maximumCvss": 10,
"minimumCvss": 10,
"subCriteria": [
"string"
],
"exclude": false,
"required": false
}
],
"limit": 25,
"offset": 0,
"includeDeleted": false
}'
See the Swagger API documentation for more details on valid request parameters.
Subcriteria#
Subcriteria are discussed in detail in the General integration guide. We provide some examples related to the Vulnerability Definitions API here, but the concepts for subcriteria are described more in detail there.
Using subcriteria allows you to fetch several different dimensions of data in one query, or express which data to exclude. By default, subqueries will be combined with an “OR” logic.
Subqueries with *exclude=true* define a set of criteria for cases to exclude:
curl -X 'POST' \
'https://api.mnemonic.no/assets/v2/vulnerability/definition/search' \
-H 'accept: application/json' \
-H 'Content-Type: application/json' \
-H "Argus-API-Key: my/api/key" \
-d '{
"includeFlags": ["deleted"],
"subCriteria": [
{
"includeFlags": ["exploitAvailable"],
"exclude": false
}
]
}'
Export#
Export is a feature of advanced search endpoints for assets, asset groups, vulnerability definitions and vulnerabilities. The user can receive a file with the data in either csv or xlsx format, it is selectable via accept header option.
The user can also configure which fields are returned in the export file, this is configurable via query parameter exportFields. Assets and Vulnerabilities have an additional option of attaching specified component values, by using exportComponents,
where the user can provide component name or UUID (for the records missing the specified component the cell will be empty). The limit and offset defaults to the same settings as the search (limit:25, offset: 0),
so to get all results the limit must be set to 0.
Example request for vulnerability search endpoint:
curl -X 'POST' \
'https://api.mnemonic.no/assets/v2/vulnerability/search?exportFields=vulnerabilityId&exportFields=severity&exportFields=definitionName&exportFields=components&exportComponents=socket' \
-H 'accept: text/csv' \
-H 'Content-Type: application/json' \
-H 'Argus-API-Key: my/api/key' \
-d '{
"customer": [
"mnemonic"
]
}'
Common Platform Enumeration (CPE)#
The Asset service ingests and mirrors the National Institute of Standards and Technology (NIST) Nation Vulnerability Database’s (NVD) product/CPE dictionary. For more information on CPEs please follow this link. Changes to existing CPEs and new CPEs are fetched from the NVD product database every two hours.
Fetching CPEs#
To fetch a single CPE you need to provide either the UUID assigned to it upon ingestion by the Asset Service or its full name :
curl -H "Argus-API-Key: my/api/key" https://api.mnemonic.no/assets/v2/cpe/bae41d20-d4af-4af0-aa7d-3bd04da402a7
curl -H "Argus-API-Key: my/api/key" https://api.mnemonic.no/assets/v2/cpe/cpe:2.3:a:Mnemonic:Argus:2
A successful request will return the CPE’s data model:
{
"id": "bae41d20-d4af-4af0-aa7d-3bd04da402a7",
"name": "Mnemonic Argus",
"part": "a",
"product": "Argus",
"vendor": "Mnemonic",
"version": "2",
"wfn": "cpe:2.3:a:Mnemonic:Argus:2:*:*:*:*:*:*:*",
"createdTimestamp": 1187903157937,
"lastUpdatedTimestamp": 1294842943723,
"flags": [
"deprecated"
],
"deprecates": [
{
"id": "3fa85f64-5717-4562-b3fc-2c963f66afa5",
"name": "Mnemonic Argus",
"wfn": "cpe:2.3:a:Mnemonic:Argus:1:*:*:*:*:*:*:*"
}
],
"deprecatedBy": [
{
"id": "3fa85f64-5717-4562-b3fc-2c963f66afa7",
"name": "Mnemonic Argus",
"wfn": "cpe:2.3:a:Mnemonic:Argus:3:*:*:*:*:*:*:*"
}
]
}
Searching for CPEs#
As with the rest of the Asset service API it is possible to search for CPEs with a simple GET request, which supports the following query parameters:
- vendor
- product
- version
- startTimestamp
- endTimestamp
- includeDeprecated
- limit
- offset
- sortBy
For example, the following request would return the first 10 products created by mnemonic:
curl -H "Argus-API-Key: my/api/key" https://api.mnemonic.no/assets/v2/cpe?limit=10&startTimestamp=0&vendor=Mnemonic
The POST search endpoint allows for more complex query logic. For the full set of fields supported by the POST search request please refer to the Swagger API documentation
Service Task management#
Asset service has an inbuilt Service Task framework that allows users, with access to specialized endpoints, to create background running tasks. One example of a Service Task creating endpoint is bulk recast vulnerabilities endpoint. Service Task generating endpoints return a task UUID of the created task, which can then be used to verify the task’s status and display details saved the task’s response context.
Fetching Service Task by UUID#
We can fetch individual Service Tasks by identifying them by their ID.
curl -X 'GET' \
'https://api.mnemonic.no/assets/v2/servicetask/{taskID}' \
-H 'accept: application/json' \
-H 'Argus-API-Key: my/api/key'
If successful, the above invocation will return the ServiceTask model which is common among all services using this framework.
ServiceTask model - detailed json
{
"id" : "32d981b2-bb08-457c-8635-f734a7e218e2",
"correlationID" : null,
"operation" : "operationName",
"state" : "running",
"parentTask" : {
"id" : "2af53030-eabf-41ae-a48c-0f4f3962e84f",
"state" : "waitingForSubtasks"
},
"flags" : [ "hasFailedSubtasks" ],
"createdByUser" : {
"type" : "user",
"id" : 1000,
"shortName" : "userShortName",
"name" : "userName",
"domain" : "mnemonic",
"customer" : "mnemonic",
"flags" : null
},
"createdTimestamp" : 10000,
"executionTimestamp" : 20000,
"finishedTimestamp" : 30000,
"workerHost" : "myhost",
"responseMessages" : [ {
"timestamp" : 15000,
"message" : "message1"
} ],
"responseContext" : {
"key" : "value"
}
}
List Service Task#
This endpoint lists service tasks using a GET operation.
curl -X 'GET' \
'https://api.mnemonic.no/assets/v2/servicetask?state=pending&operation=string&limit=25&offset=0' \
-H 'accept: application/json' \
-H 'Argus-API-Key: my/api/key'
A ResultSet containing ‘ServiceTask’ objects is returned.
Search Service Task#
This endpoint lists service tasks using a POST operation with search criteria. One example of a service task search is:
curl -X 'POST' \
'https://api.mnemonic.no/assets/v2/servicetask/search' \
-H 'accept: application/json' \
-H 'Argus-API-Key: my/api/key' \
-d '{
"operation": [
"BulkObservationRecastTask"
],
"state": [
"pending"
],
"user": [
"awesomePerson"
],
"parentTask": [
"3fa85f64-5717-4562-b3fc-2c963f66afa6"
],
"startTimestamp": 9007199254740991,
"endTimestamp": 9007199254740991,
"timeFieldStrategy": [
"all"
],
"timeMatchStrategy": "any",
"limit": 1073741824,
"offset": 1073741824
}'
A ResultSet containing ‘ServiceTask’ objects is returned.
Abort Service Task#
This endpoint aborts the running task using a DELETE operation with a service task ID
curl -X 'DELETE' \
'https://api.mnemonic.no/assets/v2/servicetask/{taskID}' \
-H 'accept: application/json' \
-H 'Argus-API-Key: my/api/key'
A ‘ServiceTask’ object of the aborted task is returned.
In the asset service, it is also possible to bulk abort tasks. The ‘bulkAbortServiceTask’ endpoint aborts service tasks using a PUT operation with search criteria. It is reusing the same request as the search endpoint ‘ServiceTaskSearchRequest’. One example is:
curl -X 'PUT' \
'https://api.mnemonic.no/assets/v2/servicetask/bulkabort' \
-H 'accept: application/json' \
-H 'Argus-API-Key: my/api/key' \
-d '{
"operation": [
"BulkObservationRecastTask"
],
"state": [
"pending"
],
"user": [
"awesomePerson"
],
"parentTask": [
"3fa85f64-5717-4562-b3fc-2c963f66afa6"
],
"startTimestamp": 9007199254740991,
"endTimestamp": 9007199254740991,
"timeFieldStrategy": [
"all"
],
"timeMatchStrategy": "any",
"limit": 1073741824,
"offset": 1073741824
}'
The endpoint returns ServiceTaskBulkAbortResponse containing information about how many tasks, fitting the criteria, was aborted successfully and how many failed to abort and why.
Metrics Collection#
Asset service has an inbuilt framework for collecting metrics about different asset data trends. The collected metrics are uploaded automatically to the metrics service. The metrics can be used to generate graphs and reports as well as to create dashboard widgets. Currently, the following descriptors are supported.
group_observation_trends#
This descriptor collects the following values:
unresolvedObservationsCount
resolvedObservationsCount
totalObservationsCount
deletedObservationsCount
The values can be grouped by following keys:
entity (asset group UUID)
definition (vulnerability identifier)
severity
asset_observation_trends#
This descriptor collects the following values:
unresolvedObservationsCount
resolvedObservationsCount
totalObservationsCount
deletedObservationsCount
The values can be grouped by following keys:
entity (asset UUID)
definition (vulnerability identifier)
severity
Pruning Customer from Asset Service#
Pruning customer data is triggered automatically via customer service. It is an internal process. It can be monitored by following relevant log messages in arguslogs and checking the status of service tasks with following operations:
pruneCustomerDataAssetGroupsFromElastic
pruneCustomerDataAssetFromElastic
pruneCustomerDataObservationsFromElastic
pruneCustomerDataAssetGroupsFromCassandra
pruneCustomerDataAssetsAndObservationsFromCassandra
pruneDataSourcesFromDB
pruneImportStatusFromDB