OAuth2 Authorization Code Flow#
The Authorization Code Flow lets the client exchange an authorization code for an ID or access token.
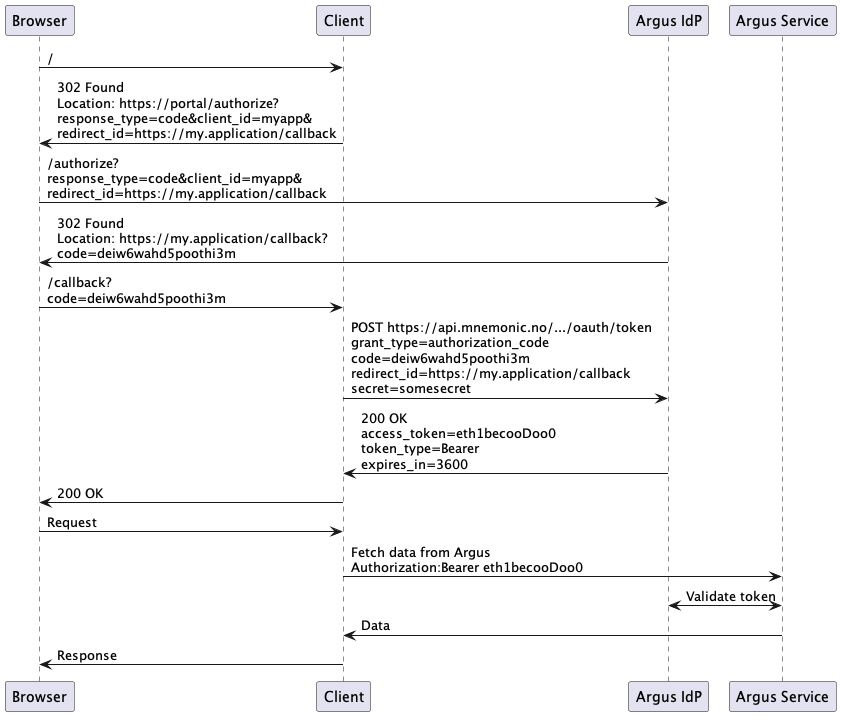
The user agent (browser) access the application, on e.g.
https://my.application, and is redirected to the Argus OAuth authorization page, requesting authorization with response type “code”:https://portal.mnemonic.no/spa/authentication/oauth/authorize?client_id=021269c5-04c3-4399-a206-32659c489803&redirect_uri=https://my.application/oauth/callback&response_type=code
If not logged into Argus, the user is redirected to the Argus Login page, and then back to the OAuth authorization page
If the current user is permitted to access the specified client, Argus issues an authorization code, and redirects the user back to the
redirectURI:https://my.application/oauth/callback?code=b11f9f83-899b-42cb-a131-790d5a40247
The external application uses the authorization code to authenticate against Argus, using a form URL-encoded
POSTrequest:curl -XPOSThttps://api.mnemonic.no/authentication/v1/oauth/token -d \ client_id=021269c5-04c3-4399-a206-32659c489803&client_secret=mySecretPassword&grant_type=authorization_code&code=b11f9f83-899b-42cb-a131-790d5a40247&redirect_uri=https://my.application/oauth/callback
Tip
Argus also supports clients sending clientID and client secret in a HTTP Basic Authorization header, which should be a base 64-encoded string:
base64(clientid + ":" + clientsecret) in a header:
Authorization: Basic MDIxMjY5YzUtMDRjMy00Mzk5LWEyMDYtMzI2NTljNDg5ODAzOm15U2VjcmV0UGFzc3dvcmQK
Argus returns a Bearer token to the client, which is a valid Argus user session, with a short lifetime.
To use this token, the OAuth client must use an
Authorization:Bearerheader:Authorization: Bearer someuser/Pheifoo1dainoofa1uede5booxe0ahQu
The OAuth client application can now use the Bearer header to issue API operations on behalf of the authorizing user.
Warning
The OAuth session must be refreshed within the refresh timeout. If at the time of refresh, the authorizing user is logged out, the OAuth session will be rejected.
The OAuth session is constrained to the permissions of the authorizing user, in addition to the constraints imposed by configuration. The session will have the permissions which constitutes the intersection of the users permissions, and the constraints configured on the client.